TekFive specializes in application-level cybersecurity and we approach this from a business risk perspective. Our teams assist organizations in assessing the cybersecurity risks they can tolerate and those they cannot, employing a comprehensive risk assessment framework. This enables companies to direct their efforts and resources toward the areas of greatest impact.
Developers Are Drowning In A Sea Of Vulnerabilities
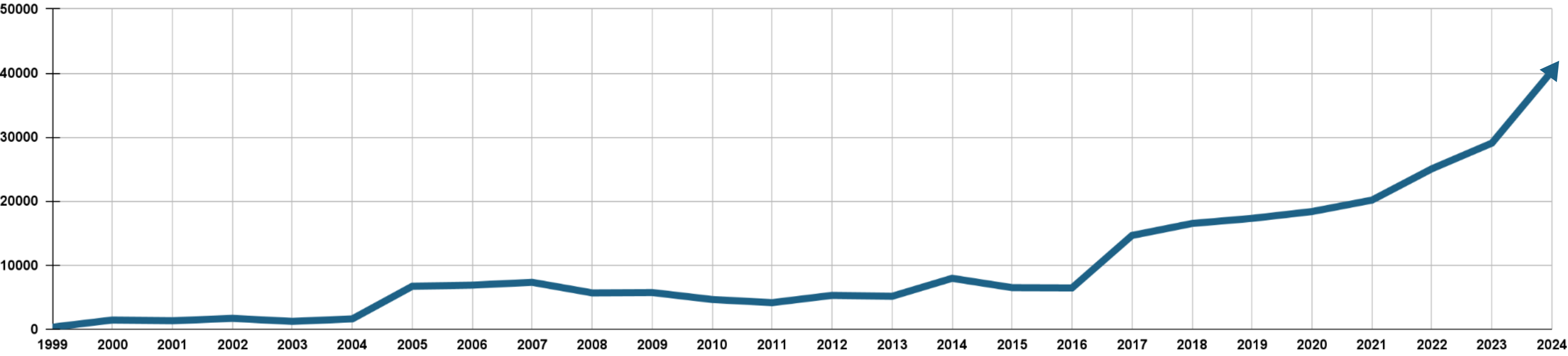
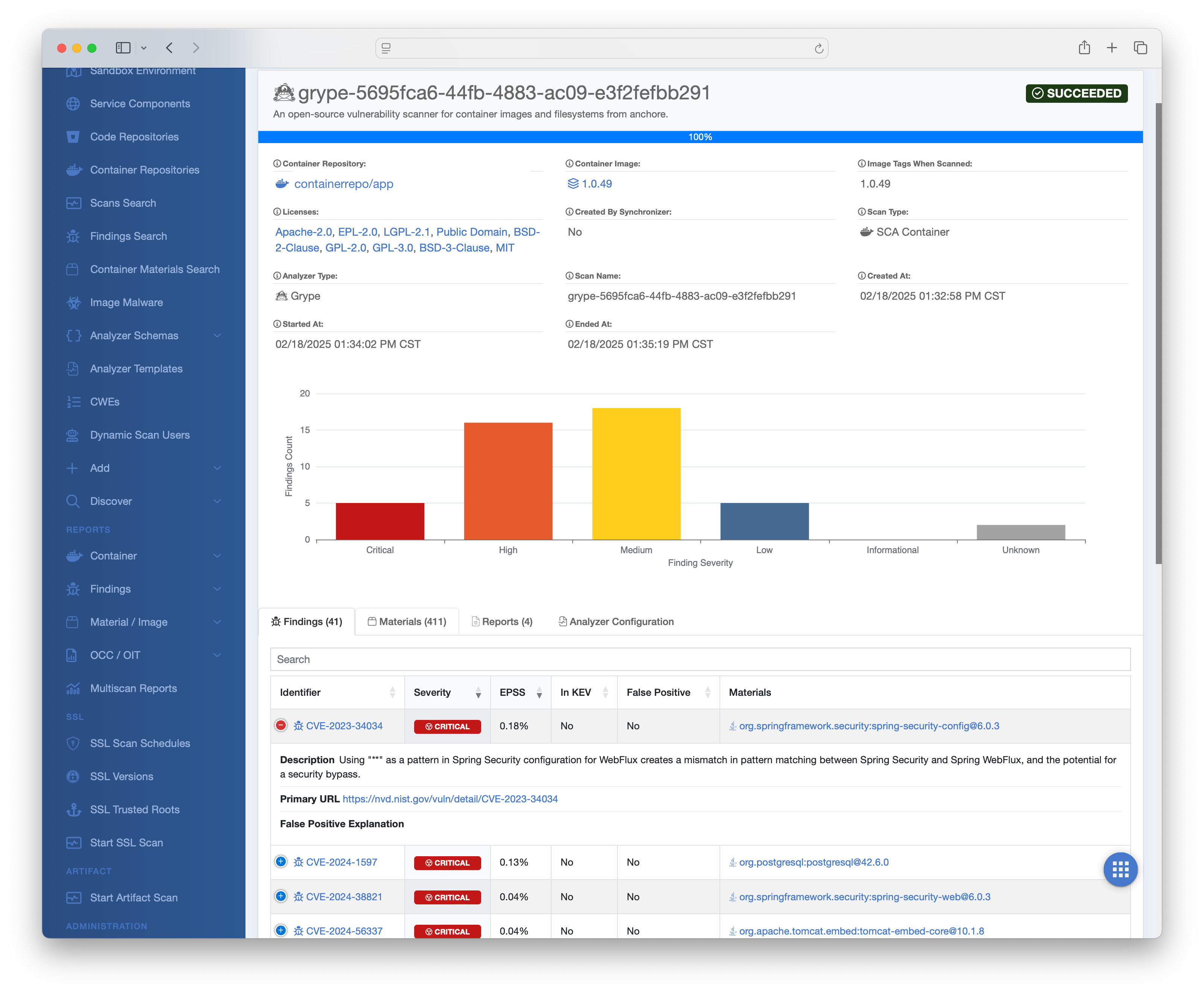
CVEs Published Each Year
Developers today are increasingly overwhelmed by the relentless flood of vulnerabilities in their apps and services that demand constant patching to keep systems secure. As the usage of open source projects increases, so do the challenges of maintaining their security updates. With thousands of new vulnerabilities identified each year, teams are often stuck in a reactive cycle, racing to apply updates across sprawling codebases, third-party libraries, and containerized environments. This burden is compounded by the pressure to maintain rapid development timelines, leaving little room for proactive security measures or innovation.
2024 Open Source Statistics (by BlackDuck)
We believe that the traditional stance of eliminating all vulnerabilities from codebases is no longer practical for most organizations. Instead, we advocate for a pragmatic approach—focusing on identifying and then prioritizing the mitigation of vulnerabilities based on actual risk not just severity. This shift acknowledges the reality that resources are finite and that not all vulnerabilities pose equal threats, allowing teams to prioritize remediation efforts where they deliver the greatest security impact while maintaining operational efficiency and innovation momentum. Our approach emphasizes four key actions.
Establish Risk Priority: We assist organizations in identifying the most critical risk factors and leverage these to create a risk-based prioritization framework. While certain government agencies are mandated to address vulnerabilities solely based on CVSS severity, we recommend that organizations adopt a broader set of metrics beyond just CVSS to determine priorities. These include EPSS (Exploit Prediction Scoring System) for predicting exploit likelihood, CISA KEV (Known Exploited Vulnerabilities) for tracking actively exploited threats, and SSVC (Stakeholder-Specific Vulnerability Categorization) for tailoring decisions to specific organizational needs and contexts.
Automate: We assist organizations in automating every facet of cybersecurity, including vulnerability detection and the seamless integration of security into CI/CD pipelines. We also automate tasks such as assigning vulnerability ownership, generating real-time risk reports, tracking remediation progress, and scheduling automated scans across systems.
Integrate: We help organizations integrate vulnerability data into their existing systems, such as Jira, by creating seamless workflows that bridge security insights with the tools teams already rely on. This is essential as it minimizes the burden of teams working across disconnected tools, enhancing efficiency and coordination.
Portfolio Awareness: Gaining insight into an organization’s application portfolio is fundamental to robust cybersecurity and operational effectiveness, offering a clear picture of the software assets in use, their dependencies, and the risks they carry. The Log4Shell vulnerabilities serve as a prime example, where numerous organizations were blindsided and struggled to accurately identify whether vulnerable versions of Log4j were present across their environments. TekFive addresses this issue by delivering specialized expertise and customized solutions to help organizations develop and sustain a comprehensive, practical understanding of their application portfolio.
Organizations should invest in capabilities that allow them to identify vulnerable systems and applications in their environments in a timely manner.
MaterialCentral
Open Source with Confidence
MaterialCentral helps Federal Agencies to effectively manage and govern open-source software use.
Enhanced Supply Chain Security - Protect application and services against known vulnerabilities and malware.
Smarter Risk Management - Use multiple severity and risk metrics such as the Exploit Prediction Scoring System (EPSS), CISA KEV and CVSS to produce a full-picture risk profile for effective prioritization and response efforts.
Deep Jira Integration - Track risk and remediation efforts in Jira along side other development tasks.